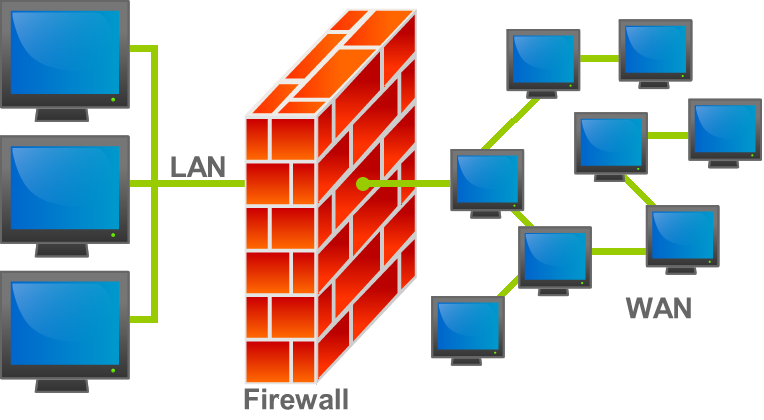
In terms of computing, a firewall is an organization security framework that screens and controls approaching and active organization traffic in light of foreordained security rules. Most of the time, a firewall separates a trusted network from an untrusted network, like the Internet.
In terms of computer security, a firewall is a piece of software that protects computers. The inside-out network traffic is monitored by this software. The protected network (trusted) and the less trusted outside network (WAN or Internet) are separated by the firewall. Each packet is subject to a set of rules in a firewall. The rules determine whether a packet can pass or is discarded. The firewall software typically runs on a computer that does nothing else when protecting a large network. A firewall safeguards one piece of the organization against unapproved access.
Packet filtering / Network Layer
The first known type of network firewall is a packet filter. A packet filter looks at the packets that are sent from one computer to another. The firewall keeps an access control list that tells what packets will be looked at and what should be done with them, if any, with silent discard as the default. A silent discard, a discard with an Internet Control Message Protocol (TCP) reset response to the sender, or a forward to the next hop are the three fundamental actions a packet can take. Packets can be filtered by source and destination IP addresses, protocol, and source and destination ports. In the 20th and early 21st centuries, the majority of Internet communication made use of well-known ports and either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). This made it possible for firewalls at the time to differentiate between specific types of traffic like web browsing, remote printing, email transmission, and file transfers.
Stateful packet inspection
This kind of firewall also keeps track of connections in addition to the straightforward packet filtering described above. A packet can initiate a brand-new connection or be a component of an existing connection. It is likely ineffective and can be thrown away if it is neither of the two.
Application layer firewalls
Application layer Firewalls examine more than just the metadata; they additionally take a gander at the genuine information moved. They understand how certain protocols operate, such as FTP or HTTP. After that, they can determine whether the data in the packet is genuine (for that protocol). This packet can be thrown out if its not.
The ability of application layer filtering to comprehend particular programs and protocols like the File Transfer Protocol (FTP), the Domain Name System (DNS), and the Hypertext Transfer Protocol (HTTP) is its primary advantage. This permits it to recognize undesirable applications or administrations utilizing a non standard port, or distinguish in the event that a permitted convention is being mishandled. It can also provide unified security management, which includes virtual private networking and enforced encrypted DNS. The next-generation firewall began offering a wider range of application-layer inspection options in 2012, including but not limited to the following:
- •Web filtering
- •User identity management
- •Intrusion prevention systems
- •Web application firewall
Endpoint specific
Endpoint based application firewalls based on endpoints work by deciding whether a process should accept any given connection. Application firewalls check connections by comparing the process ID of data packets to a set of rules that apply to the local process that is transmitting the data. Application firewalls achieve their capability by guiding into attachment calls to channel the associations between the application layer and the lower layers. Socket filters are another name for application firewalls that respond to socket calls.







































